convert hex to public key
Decoding Digital Identities: Converting Hex to Public Keys
Source: sectigostore.com
Ever felt like you're looking at a secret code, a digital language spoken only by computers? Well, sometimes, that secret code is a public key, a vital piece of information in the digital world! This guide will help you understand how to unlock these digital identities by translating a hexadecimal string (that jumbled set of hex characters) into a usable public key.
What's a Public Key Anyway?
Think of a public key like a special address for your digital persona. It's how people can send secure messages to you without knowing your private key – the secret behind the scenes. It's an essential part of many secure processes like encrypting email and securely sending data (think using your secure messaging apps and payment transactions) .
Why Hex?
Hexadecimal (often just called 'hex') is a clever way to represent binary data in a more compact and readable way. Instead of using long strings of 0s and 1s, hex uses numbers and letters (0-9, A-F) making things easier for us humans. Imagine that binary sequence in gigabytes size. How complex will it look!
Why Should I Care About This?
Knowing how to do this might feel tricky, and yes it can be at first glance. However, with a good guide (this one!), you will feel less intimidated by these technologies and secure transactions that need them. It’s understanding building blocks, you see.
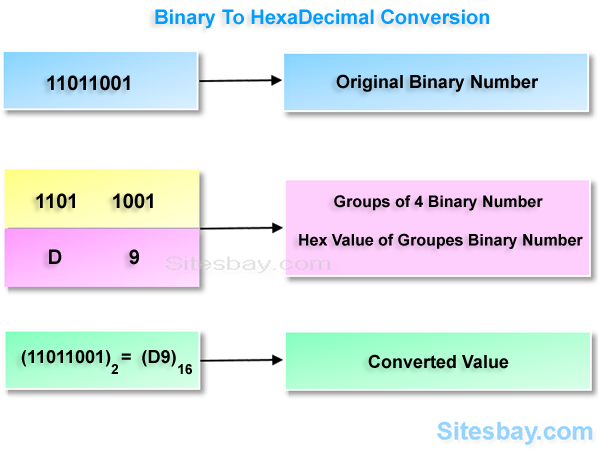
Source: sitesbay.com
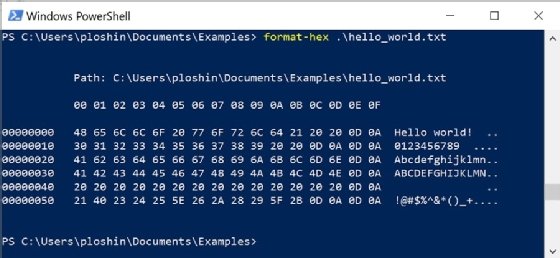
The Hexadecimal Jungle: Decoding the Code
First, let's get comfortable with hex numbers. A hexadecimal number like "0x2A" means something very different than '2A' standing alone. That's an important point, use of '0x' signifier, that will be necessary in converting the hexadecimal representation of the public key data into the actual public key in its required format.
Key Questions About Hexadecimal
-
What does '0x' mean? The '0x' part in front of a hexadecimal number identifies it as hexadecimal. It's kind of like a tag telling you to handle that hex character a specific way. (So remember '0x') .
-
What are the digits involved? Hex uses numbers (0–9) and letters (A–F). Each letter corresponds to a numerical value, see example.
-
How long is a hexadecimal representation usually? (Important to know for verification!) Length of the public key's representation can range in this conversion process..
Breaking Down the Steps (How To Convert!)
Let's convert! There are two steps in doing that and tools out there.
-
Identifying Your Hex String: Find your hexadecimal public key value in the given string or result that will become useful after conversions (which we need) to obtain this value
-
Using a Converter Tool: Thankfully, lots of websites (that can be a part of tools, which a simple search engine search result shows. Just check carefully that its secured if used online to protect your info (the private or the data needed). A good converter can take this long hex-value string as input. Or you can use programming languages that can make use of dedicated methods or libraries provided (Python examples could also be a possible source). Check for input and outputs type. Input must match conversion instructions of used method or library and result has the form of a key format required). Use these carefully, for secured purposes and in appropriate places! (Be Careful, only use secured converters.)
Example:
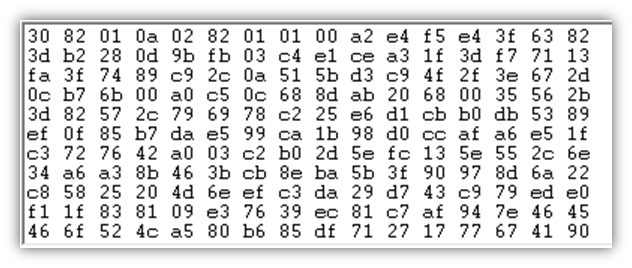
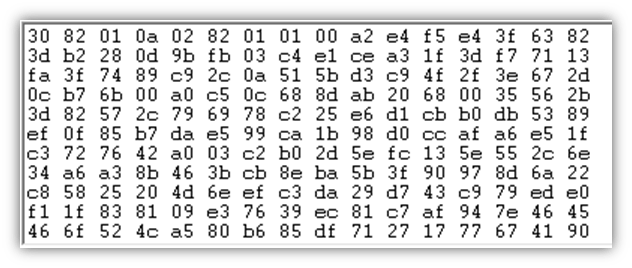
Input: 0x04B947CFB190F992D339AF2CAFE0B7D7F8DF86FA3B5B9F796E02E306E6F40AFDF49
(Input is the key you want to convert )
Output: Some programs produce a specific format! Make sure they produce correct key value(the important key you need), otherwise it can have other useful uses depending on situation (though there is the main important purpose for obtaining). Your purpose or requirement for this conversion decides what value output you would need. -
Verification: Make sure you carefully verify result!
-
Matching Lengths: Public keys (if this were for a cryptocurrency like Bitcoin or similar technologies) in certain contexts or systems have standard lengths in bits. Verify that converted values also follow that format length in bit representation to understand better if its correctly processed for usage.
-
Data Structure Consistency: If in an application context, match formats expected! (Sometimes expected to follow in a particular order to use and match correctly for its purpose, etc). If using application program check formats involved, match lengths in correct structures before moving to step four .
-
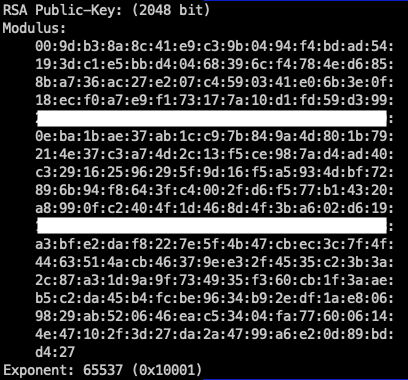
Source: baptistout.net
Deconstructing Common Problems
-
Problem: I don't know what's inside this given hex string input.
-
Solution: Consult related manuals or documentation regarding given hexadecimal string.
-
Problem: Result after conversion differs greatly than expected key structure
-
Solution: Re-check conversion inputs and parameters , or input values. Carefully evaluate inputs again.
Source: sandilands.info
Understanding Your Converted Public Key
After successfully decoding your public key from a hexadecimal format into readable format, use cases include digital signatures for verifying messages. They also use in other crytographic systems, like Blockchain cryptocurrency, etc… Knowing your public key provides security on transactions!